The following table shows how Surety’s hash-and-link trusted time-stamp technology compares with other commonly used data integrity protection mechanisms. Detailed comparison reports of AbsoluteProof with each these technologies are available for download in our Comparison Summary Sheets box to the right.
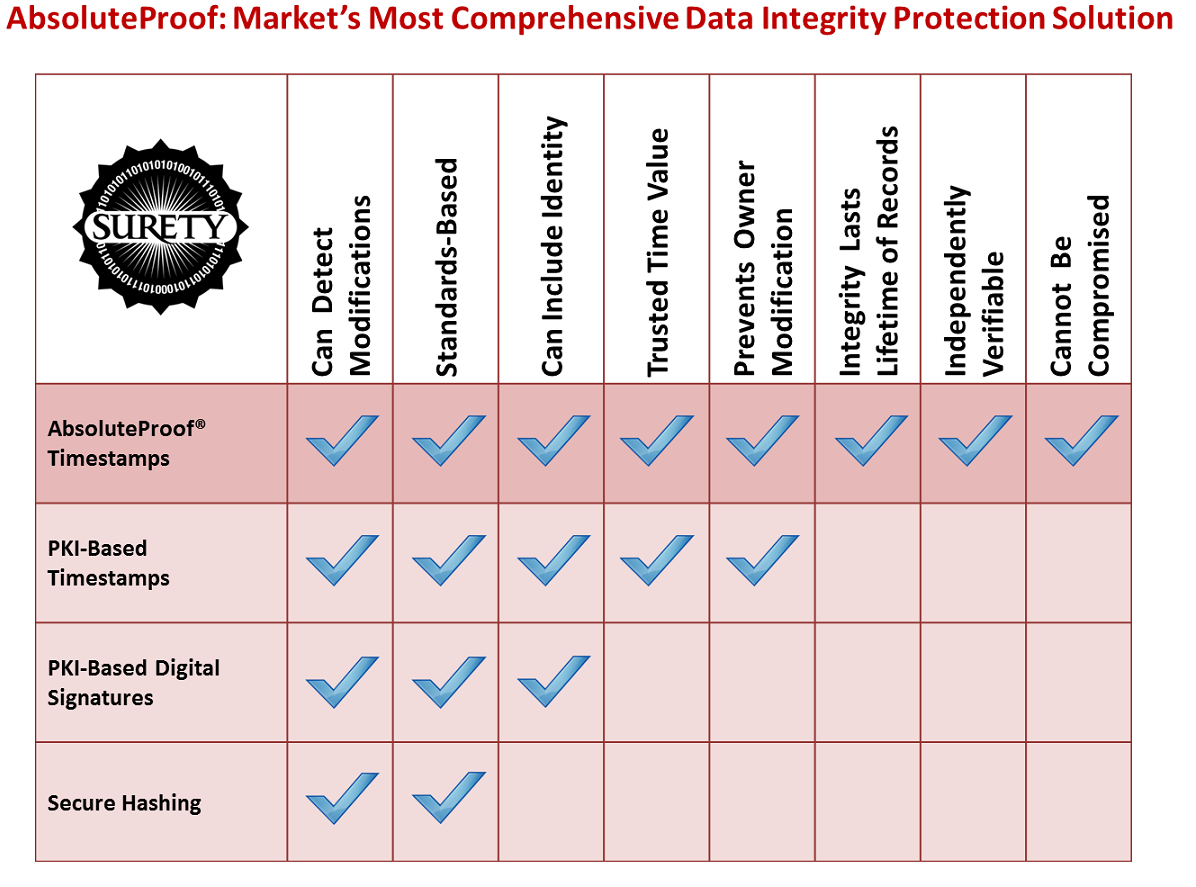
AbsoluteProof® offers trusted time value, is portable, offers long-lived integrity, detects tampering, is independently verifiable, is standards-based and cannot be compromised — a package of capabilities that secure hashing, PKI timestamps and PKI digital signature cannot offer.